Protect your store, data, and customers with enterprise-grade eCommerce security in Medusa.
Why eCommerce security matters in 2026
Ecommerce platforms rank among the most targeted digital services.
Attackers focus on web services that process login credentials, payment details, and personal data, using increasingly sophisticated vectors such as ransomware, phishing, and credential theft. Attack vectors (ransomware, phishing, credential theft) continue to evolve, meaning traditional defenses alone are no longer sufficient in 2026.
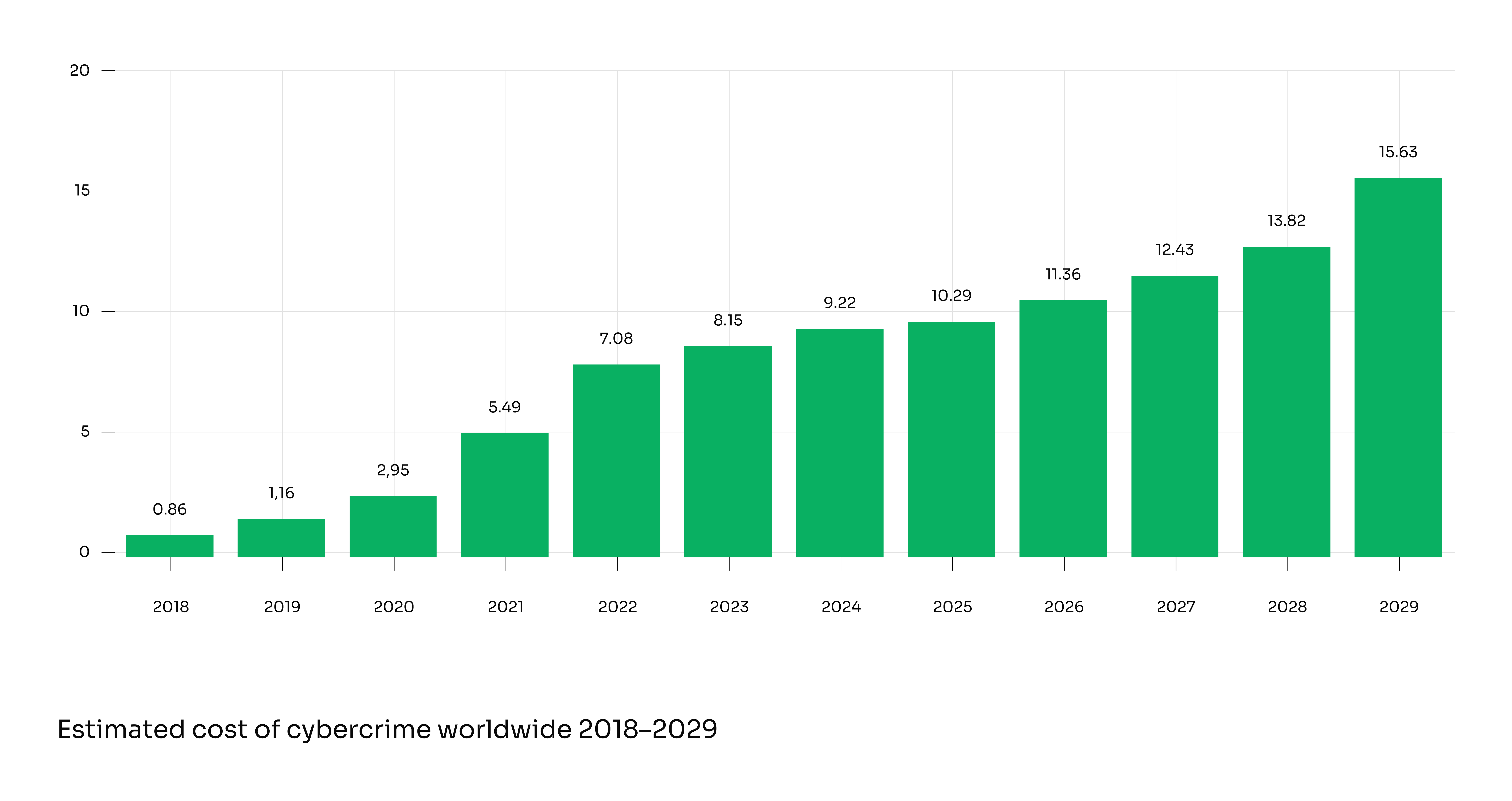
The financial impact of cybercrime continues to grow. Global costs from cybercrime are projected to exceed $15.6 trillion by 2029, reflecting cumulative costs from theft, fraud, disruption, and remediation across industries.
This trend highlights the urgency of proactive security measures for eCommerce infrastructure.
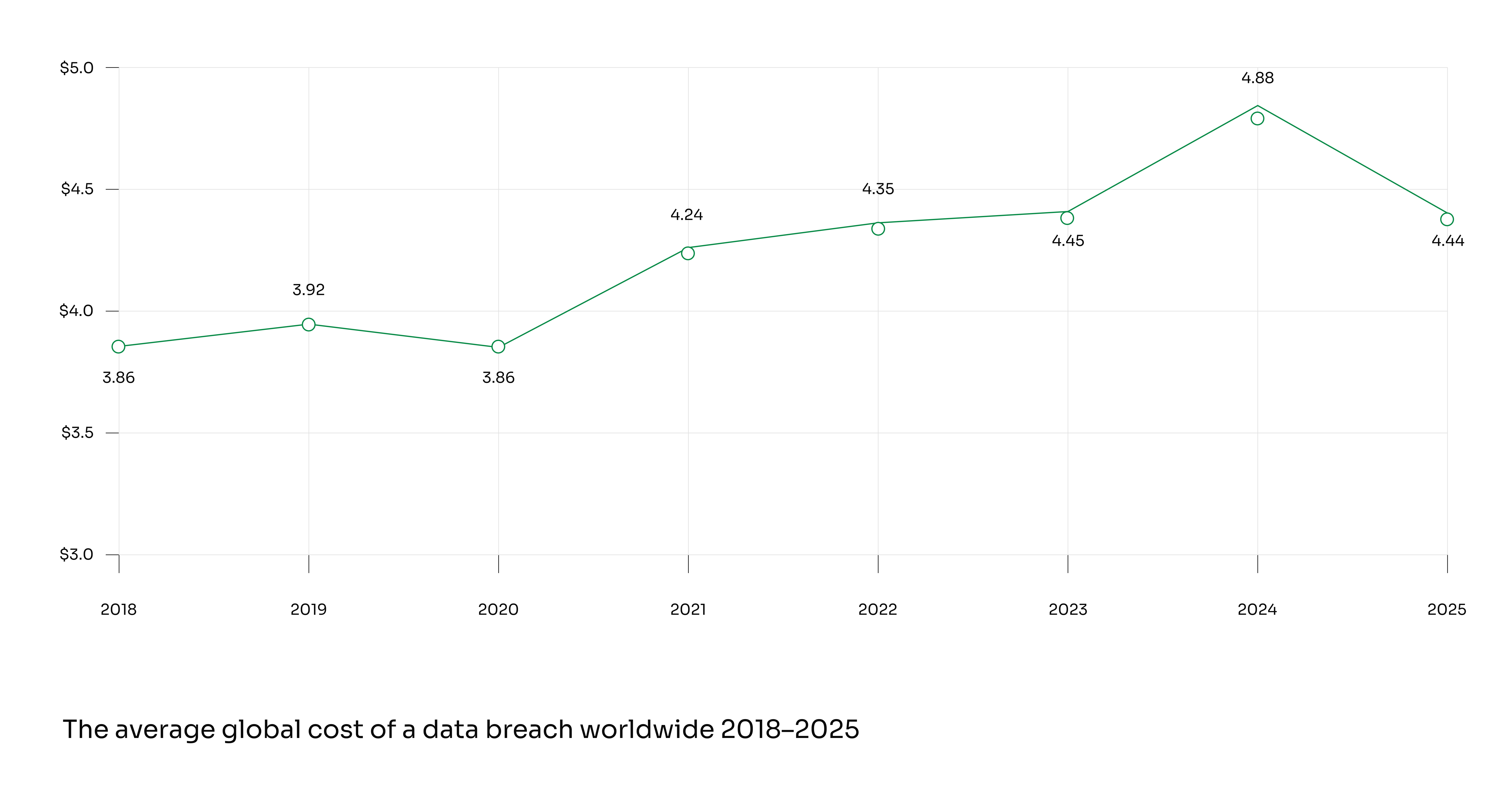
In the most recent data available, the average global cost of a data breach reached approximately $4.44 million in 2025, encompassing detection, legal exposure, and operational loss.
Emerging technologies also introduce new risks: studies show that 97% of organizations reporting AI-related security incidents lacked proper AI access controls, indicating gaps in defenses as attackers leverage automation and AI-driven techniques.
Regulatory pressure and trust are now non-negotiable.
Standards such as PCI DSS require strong controls for storing and processing payment card data, and frameworks like GDPR (General Data Protection Regulation) impose stringent requirements for protecting personal data and reporting breaches. Failure to comply not only incurs fines but also degrades customer trust, which directly correlates with conversion rates and long-term revenue.
In short, the cost of breaches, the evolution of attack methods, and tightening regulatory requirements make eCommerce security an operational imperative for any online business in 2026.
What you'll find inside this eCommerce security whitepaper
- Top eCommerce security threats & trends to watch in 2026
- The Medusa Security Plan for enterprise eCommerce deployments
- Medusa’s architecture and platform-level security features
- Vendors' platform-level security checklist for CTOs
- Attack scenarios and security failure patterns from real eCommerce businesses
- Business impact of security failures on operations, revenue, and trust
- Best practices to secure any eCommerce platform
- High-level mitigation strategies
Top eCommerce security threats you can't ignore
Ecommerce platforms expose multiple attack surfaces: public storefronts, APIs, admin panels, third-party integrations, and payment flows. The threats below consistently appear in real production incidents and website security audits across eCommerce environments.
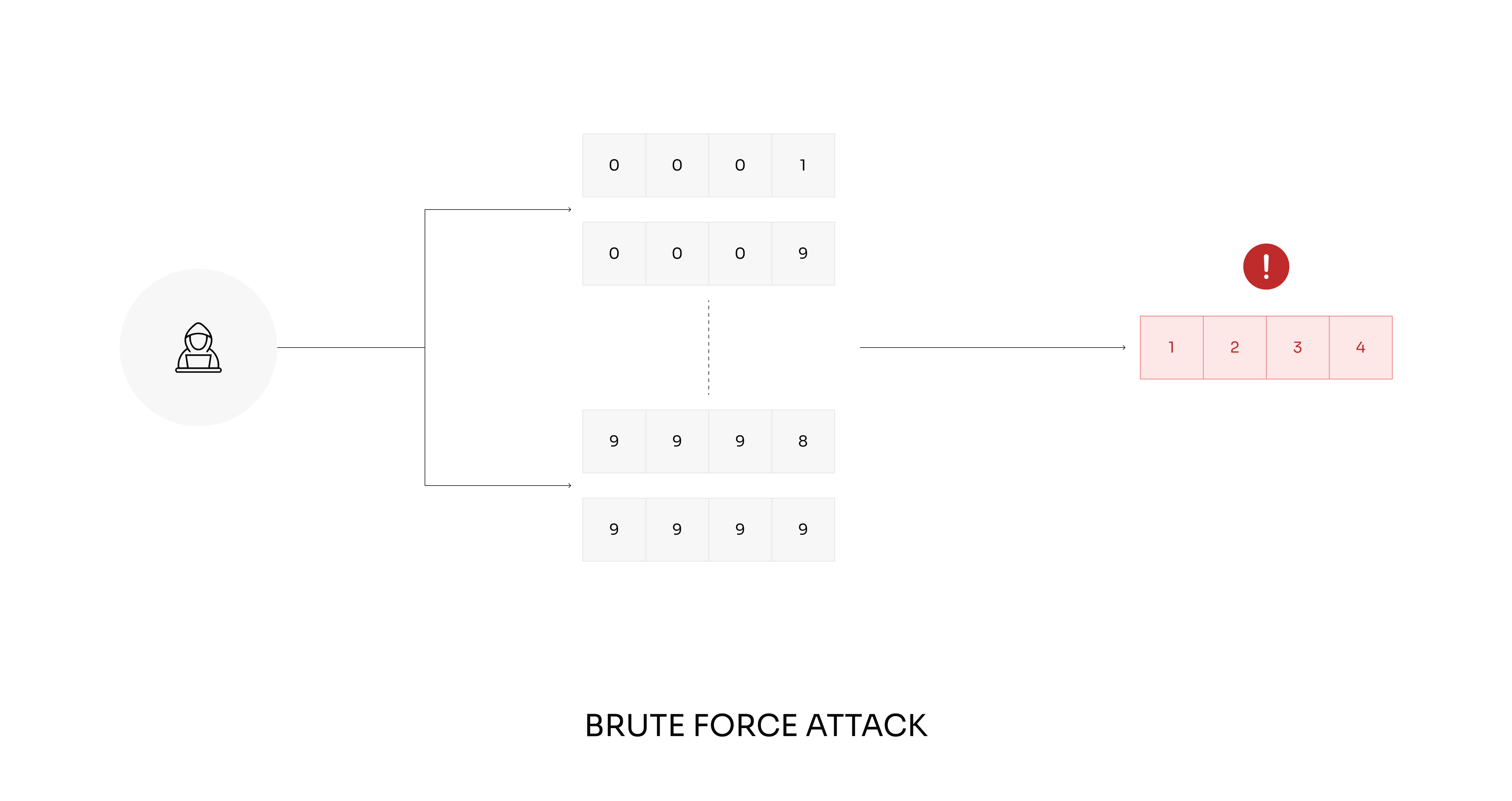
Brute-force attacks
Automated attempts to guess login credentials targeting admin panels, customer accounts, and APIs. Often combined with credential stuffing using leaked password databases.
Distributed Denial of Service (DDoS)
Traffic floods are designed to overwhelm web servers, APIs, or payment gateways. DDoS attacks directly affect availability, checkout flows, and revenue continuity.
.png)
Payment fraud and card skimming
Injection of malicious code into checkout or payment flows to capture credit card details and payment data before encryption or tokenization.
Malware and ransomware
Malicious software used to gain persistence, encrypt infrastructure, or exfiltrate sensitive data. Often introduced through compromised dependencies or misconfigured servers.
AI-assisted attacks
Use of AI agents to credential stuffing and password cracking, deepfakes and biometric spoofing, or automate phishing across APIs and admin interfaces.
See the full threat map in Section 3! Download whitepaper!
How to evaluate eCommerce platform's security
Use this micro-checklist to identify security gaps early, before platform adoption or migration, when architectural decisions are hardest to reverse. Each point addresses a common failure mode observed in eCommerce security breaches.
- Can one store or brand access another tenant’s data due to misconfiguration?
- Are databases, caches, and storage explicitly tenant-aware?
- Does the platform support role-based access control (RBAC)?
- Is multi-factor authentication (MFA) available for admin and operator accounts?
- Are dependencies and third-party libraries scanned for vulnerabilities?
- Is all traffic encrypted using TLS?
- Are encryption keys managed and rotated securely?
Get a clear list of actions to keep your eCommerce secure. Download checklist!
Who is this guide for?
- CTOs and Security Engineers designing and reviewing secure eCommerce platforms
- Platform Owners responsible for protecting customer data, payment flows, and overall eCommerce security posture
- Technical Leaders implementing security measures, access control, and incident response processes in eCommerce systems
- Compliance and Risk Managers aligning eCommerce platforms with PCI DSS, GDPR, and data protection requirements
Why Medusa is secure by design
- Modular, headless architecture that limits attack surface and isolates critical components.
- Platform-level security controls, not optional plugins or external add-ons.
- Role-based access control (RBAC) and environment separation to protect sensitive operations.
- Secure defaults enabled by design: HTTPS, tokenization, logging, and rate limiting.
- API-first security with validation, throttling, and token expiration.
- Dependency and third-party code isolation to reduce supply-chain risk.
Explore how these mechanisms work in detail in Sections 7 & 8 of the whitepaper!
Security expertise behind this guide
This guide is based on hands-on experience from teams building (Rigby) and securing (LogicalTrust) real eCommerce systems.
Presented recommendations are informed by security consultations with LogicalTrust, a company specializing in IT security. They delivered 700+ security tests across a wide range of systems and industries that identified over 9,900 vulnerabilities – often due to repeatable design and process gaps.
The guidance in this whitepaper aligns with widely recognized security standards and frameworks, including OWASP and PCI DSS, and focuses on applying these principles in real-world eCommerce environments.